When surfing around the net coming from a property Personal computer, there are various components that make the complete process feasible. First of all, on a single finish, we have our property Personal computer. This Laptop or computer is linked via its modem to the ISP’s server, which often is interconnected to servers all over the world that host the precise web sites we are seeking.
From your web internet browser, we send out a request to access a unique website by typing the site’s address, by way of example, if we strike Key in, this demand is sent to our ISP’s server, which pinpoints the request. When the ISP has a proxy server with cached demands, when retrieving our require it would look up the information in their cache to find out if the proxy can comply or otherwise. This means that the proxy server saves all demands made out of consumers to the cache, in order that the next time yet another end user makes the very same demand, it lacks to access that exact same details from the initial server. The proxy server does respond by mailing the data to our PC looking at the cache.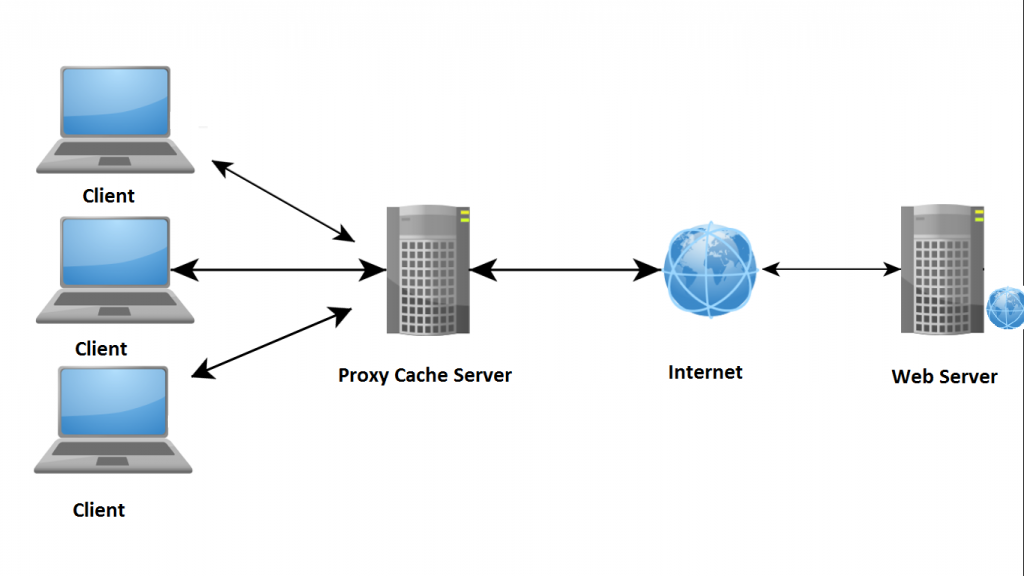
Alternatively, in the event the proxy server cannot comply, it will send out the demand for the real server that hosts the actual website we are asking for. The variety server transmits those details to the proxy server, which could then cache the answer for long term requests, and then sends the info to the Computer. At times, multiple proxy servers may be included, as some web sites, like MSN, Yahoo, and AOL have a number of proxy servers that respond to needs using their cache, therefore reducing the amount of petitions towards the major server and minimizing reply times.
Within a corporate and business system, even more factors develop portion of the approach. In addition to the chance of having its own proxy server to enhance overall performance, the proxy also can work as a filtration from the employees’ terminal, blocking attempts to gain access to certain content using their web browsers. Navigate to this site https://www.chartattack.com/how-do-i-remain-anonymous-online/. In addition, organizations have postal mail servers that retail store and deliver email messages more than its local group and WAN. All possible computer viruses are filtered during this period before it might achieve an employee’s PC. Servers provide more stability by way of firewalls either in the proxy by itself or from a firewall server dedicated to these kinds of
